nessa noticia fala que a falha é nos processadores Intel; ARM e nos AMD afinal os AMD também têm a falha?Microsoft issues emergency Windows update for processor security bugs
https://www.theverge.com/2018/1/3/1...t=chorus&utm_medium=social&utm_source=twitter
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Processador Vulnerabilidade MeltDown / Spectre (aka Kaiser bug)
- Autor do tópico Nemesis11
- Data Início
https://www.cnbc.com/2018/01/03/amd-rebukes-intel-says-flaw-poses-near-zero-risk-to-its-chips.html
"Chipmaker Advanced Micro Devices on Wednesday pushed back on a statement from Intel about a recently documented security flaw, saying its chips are mainly not affected."
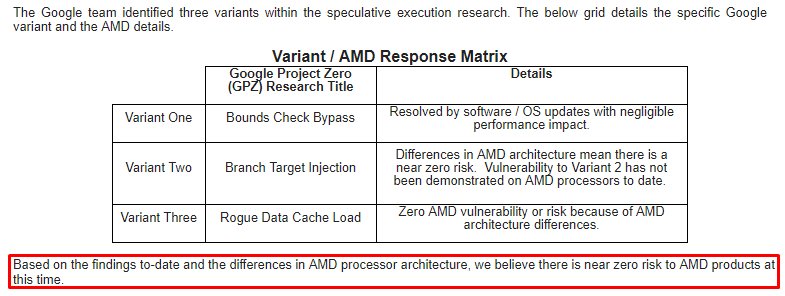
"To be clear, the security research team identified three variants targeting speculative execution. The threat and the response to the three variants differ by microprocessor company, and AMD is not susceptible to all three variants. Due to differences in AMD's architecture, we believe there is a near zero risk to AMD processors at this time."
E mais...
https://twitter.com/ryanshrout/status/948650502664974337
A Intel está simplesmente a tentar fazer as pessoas acreditar que não é a unica afectada. Jogo de palavras
"Chipmaker Advanced Micro Devices on Wednesday pushed back on a statement from Intel about a recently documented security flaw, saying its chips are mainly not affected."
"To be clear, the security research team identified three variants targeting speculative execution. The threat and the response to the three variants differ by microprocessor company, and AMD is not susceptible to all three variants. Due to differences in AMD's architecture, we believe there is a near zero risk to AMD processors at this time."
E mais...
https://twitter.com/ryanshrout/status/948650502664974337
A Intel está simplesmente a tentar fazer as pessoas acreditar que não é a unica afectada. Jogo de palavras

Última edição:
Nemesis11
Power Member
Respostas da AMD, ARM, Google e Microsoft:
https://www.axios.com/how-the-giant...-a-massive-chip-vulnerability-2522206367.html
Microsoft:
Microsoft is updating Windows 10 today with a special fix for the issue and also making available updates for Windows 7 and Windows 8.
"We're aware of this industry-wide issue and have been working closely with chip manufacturers to develop and test mitigations to protect our customers. We are in the process of deploying mitigations to cloud services and have also released security updates to protect Windows customers against vulnerabilities affecting supported hardware chips from Intel, ARM, and AMD. We have not received any information to indicate that these vulnerabilities had been used to attack our customers."
Researchers from Google's Project Zero found the vulnerabilities last year and reported them to Intel, AMD and ARM in June 2017. In a blog post, Google disclosed what product actions it is taking with regards to Android, Chrome OS and the Google Cloud. It said other products, such as Chromecast and the Chrome browser aren't affected.
AMD:
"To be clear, the security research team identified three variants targeting speculative execution. The threat and the response to the three variants differ by microprocessor company, and AMD is not susceptible to all three variants. Due to differences in AMD's architecture, we believe there is a near zero risk to AMD processors at this time. We expect the security research to be published later today and will provide further updates at that time."
ARM:
"Arm (has) been working together with Intel and AMD to address a side-channel analysis method which exploits speculative execution techniques used in certain high-end processors, including some of our Cortex-A processors. This method requires malware running locally and could result in data being accessed from privileged memory. Please note that our Cortex-M processors, which are pervasive in low-power, connected IoT devices, are not impacted.
https://www.axios.com/how-the-giant...-a-massive-chip-vulnerability-2522206367.html
Nemesis11
Power Member
Disclosure dos 3 Bugs, com detalhes:
https://googleprojectzero.blogspot.pt/2018/01/reading-privileged-memory-with-side.html
https://spectreattack.com/spectre.pdf
https://meltdownattack.com/meltdown.pdf
Reading privileged memory with a side-channel
Posted by Jann Horn, Project Zero
We have discovered that CPU data cache timing can be abused to efficiently leak information out of mis-speculated execution, leading to (at worst) arbitrary virtual memory read vulnerabilities across local security boundaries in various contexts.
Variants of this issue are known to affect many modern processors, including certain processors by Intel, AMD and ARM. For a few Intel and AMD CPU models, we have exploits that work against real software. We reported this issue to Intel, AMD and ARM on 2017-06-01 [1].
So far, there are three known variants of the issue:
- Variant 1: bounds check bypass (CVE-2017-5753)
- Variant 2: branch target injection (CVE-2017-5715)
- Variant 3: rogue data cache load (CVE-2017-5754)
Before the issues described here were publicly disclosed, Daniel Gruss, Moritz Lipp, Yuval Yarom, Paul Kocher, Daniel Genkin, Michael Schwarz, Mike Hamburg, Stefan Mangard, Thomas Prescher and Werner Haas also reported them; their [writeups/blogposts/paper drafts] are at:
https://googleprojectzero.blogspot.pt/2018/01/reading-privileged-memory-with-side.html
https://spectreattack.com/spectre.pdf
https://meltdownattack.com/meltdown.pdf
Nemesis11
Power Member
Processadores afectados:
Which systems are affected by Meltdown?
"Desktop, Laptop, and Cloud computers may be affected by Meltdown. More technically, every Intel processor which implements out-of-order execution is potentially affected, which is effectively every processor since 1995 (except Intel Itanium and Intel Atom before 2013). We successfully tested Meltdown on Intel processor generations released as early as 2011. Currently, we have only verified Meltdown on Intel processors. At the moment, it is unclear whether ARM and AMD processors are also affected by Meltdown.
Which systems are affected by Spectre?
Almost every system is affected by Spectre: Desktops, Laptops, Cloud Servers, as well as Smartphones. More specifically, all modern processors capable of keeping many instructions in flight are potentially vulnerable. In particular, we have verified Spectre on Intel, AMD, and ARM processors."
https://meltdownattack.com/
https://spectreattack.com/
Which systems are affected by Meltdown?
"Desktop, Laptop, and Cloud computers may be affected by Meltdown. More technically, every Intel processor which implements out-of-order execution is potentially affected, which is effectively every processor since 1995 (except Intel Itanium and Intel Atom before 2013). We successfully tested Meltdown on Intel processor generations released as early as 2011. Currently, we have only verified Meltdown on Intel processors. At the moment, it is unclear whether ARM and AMD processors are also affected by Meltdown.
Which systems are affected by Spectre?
Almost every system is affected by Spectre: Desktops, Laptops, Cloud Servers, as well as Smartphones. More specifically, all modern processors capable of keeping many instructions in flight are potentially vulnerable. In particular, we have verified Spectre on Intel, AMD, and ARM processors."
https://meltdownattack.com/
https://spectreattack.com/
Nemesis11
Power Member
Eu gosto desta parte do FAQ:
Can I detect if someone has exploited Meltdown or Spectre against me?
Probably not. The exploitation does not leave any traces in traditional log files.
Has Meltdown or Spectre been abused in the wild?
We don't know.
É bom saber.....
Can I detect if someone has exploited Meltdown or Spectre against me?
Probably not. The exploitation does not leave any traces in traditional log files.
Has Meltdown or Spectre been abused in the wild?
We don't know.
É bom saber.....
Nemesis11
Power Member
No primeiro post tinha colocado que o CEO da Intel tinha vendido 11 milhões de $ em ações da Intel em fins de Novembro. Na verdade, ele vendeu 24 milhões de $ ao todo. 11 milhões eram ações que ele tinha. O resto veio de options que ele podia exercer.
Mais dois pormenores. Pelos estatutos da Intel, o CEO tem que possuir pelo menos 250 mil ações da Intel. Ele, no fim de Novembro, vendeu tudo o que podia vender, tanto em ações que tinha, como em options e ficou com o mínimo essencial, isto é, as 250 mil ações que tem mesmo que possuir.
O segundo pormenor é que, nestes cargos, não se pode decidir no dia que se quer em vender as ações. Há uma janela de tempo em que se pode vender e tem que se decidir com antecedência. E assim foi. No entanto, ele decidiu vender tudo em fins de Outubro, quando a Intel já sabia do Bug.
http://www.businessinsider.com/inte...fter-company-was-informed-of-chip-flaw-2018-1
Isto parece ser um caso claro de "Insider Trading", quando alguém dentro da empresa decide tomar uma decisão a nível pessoal, porque tem conhecimento de factos importantes que alteram a cotação de uma empresa.
A Intel, no fim de 2017, teve uma subida grande e rápida, a nível da sua cotação, em relação ao valor do inicio do ano. Se não estou em erro, de 35%. O CEO aproveitou vender, antes das más noticias.
Enfim, o pior é que no final, não lhe deve acontecer nada.
Mais dois pormenores. Pelos estatutos da Intel, o CEO tem que possuir pelo menos 250 mil ações da Intel. Ele, no fim de Novembro, vendeu tudo o que podia vender, tanto em ações que tinha, como em options e ficou com o mínimo essencial, isto é, as 250 mil ações que tem mesmo que possuir.
O segundo pormenor é que, nestes cargos, não se pode decidir no dia que se quer em vender as ações. Há uma janela de tempo em que se pode vender e tem que se decidir com antecedência. E assim foi. No entanto, ele decidiu vender tudo em fins de Outubro, quando a Intel já sabia do Bug.
Intel was aware of the chip vulnerability when its CEO sold off $24 million in company stock
- Intel CEO Brian Krzanich sold off $24 million worth of stock and options in the company in late November.
- The stock sale came after Intel was informed by Google of a significant vulnerability in its chips — a flaw that only became public this week.
- Intel says the stock sale was unrelated to the vulnerability, but came as part of a planned divestiture program. But Krzanich put that stock sale plan in place in October — several months after Intel was informed of the vulnerability.
http://www.businessinsider.com/inte...fter-company-was-informed-of-chip-flaw-2018-1
Isto parece ser um caso claro de "Insider Trading", quando alguém dentro da empresa decide tomar uma decisão a nível pessoal, porque tem conhecimento de factos importantes que alteram a cotação de uma empresa.
A Intel, no fim de 2017, teve uma subida grande e rápida, a nível da sua cotação, em relação ao valor do inicio do ano. Se não estou em erro, de 35%. O CEO aproveitou vender, antes das más noticias.
Enfim, o pior é que no final, não lhe deve acontecer nada.
mcog_blaster
Power Member
Eu gosto desta parte do FAQ:
Has Meltdown or Spectre been abused in the wild?
We don't know.
É bom saber.....
Bém provavel que sim.
https://twitter.com/MalwareJake/status/948756142586548224
https://twitter.com/misc0110/status/948706387491786752
Do que entendi os únicos AMD que eles testaram foram "Bulldozer"
não se sabe assim se os ZEN são afectados ou não (os CPU testados apenas são vulneráveis ao Spectre 1), supostamente com o ZEN foi introduzida uma função de "memory encription" descrita neste whitepaper.
Entretanto os gajos do the register voltaram à carga
- We translated Intel's crap attempt to spin its way out of CPU security bug PR nightmare
- Meltdown, Spectre: The password theft bugs at the heart of Intel CPUs
neste último artigo do Register, a informação parece algo contraditória:
Pelo meio têm aparecido os habituais "comentários" do Linus Torvalds
Entretanto a ARM já tem disponível uma página com a informação
https://developer.arm.com/support/security-update
EDIT: o pior para a Intel é isto vir quse 2 meses depois de ter sido descoberto um outro
Intel finds critical holes in secret Management Engine hidden in tons of desktop, server chipsets
https://googleprojectzero.blogspot.pt/Tested Processors
- Intel(R) Xeon(R) CPU E5-1650 v3 @ 3.50GHz (called "Intel Haswell Xeon CPU" in the rest of this document)
- AMD FX(tm)-8320 Eight-Core Processor (called "AMD FX CPU" in the rest of this document)
- AMD PRO A8-9600 R7, 10 COMPUTE CORES 4C+6G (called "AMD PRO CPU" in the rest of this document)
- An ARM Cortex A57 core of a Google Nexus 5x phone [6] (called "ARM Cortex A57" in the rest of this document)
não se sabe assim se os ZEN são afectados ou não (os CPU testados apenas são vulneráveis ao Spectre 1), supostamente com o ZEN foi introduzida uma função de "memory encription" descrita neste whitepaper.
Entretanto os gajos do the register voltaram à carga
- We translated Intel's crap attempt to spin its way out of CPU security bug PR nightmare
- Meltdown, Spectre: The password theft bugs at the heart of Intel CPUs
neste último artigo do Register, a informação parece algo contraditória:
Here's a summary of the two branded bugs:
Meltdown
- It affects potentially all out-of-order execution Intel processors since 1995, except Itanium and pre-2013 Atoms. It definitely affects out-of-order x86-64 Intel CPUs since 2011. There are workaround patches to kill off this vulnerability available now for Windows, and for Linux. Apple's macOS has been patched since version 10.13.2. Installing and enabling the latest updates for your OS should bring in the fixes. You should go for it. If you're a Windows Insider user, you're likely already patched. Windows Server admins must enable the kernel-user space splitting feature once it is installed; it's not on by default.
- It also affects Arm Cortex-A75 cores. Qualcomm's upcoming Snapdragon 845 is an example part that uses the A75. There are Linux kernel KPTI patches available to mitigate this. The performance hit isn't known, but expected to be minimal.
- Additionally, Cortex-A15, Cortex-A57 and Cortex-A72 cores suffer from a variant of Meltdown: protected system registers can be accessed, rather than kernel memory, by user processes. Arm has a detailed white paper and product table, here, describing all its vulnerable cores, the risks, and mitigations.
- Meltdown does not affect any AMD processors.
Aqui diz que também afecta o ZEN.Spectre
- It is a very messy vulnerability that is hard to patch, but is also tricky to exploit. It's hard to patch because just installing the aforementioned KPTI features is pointless on most platforms – you must recompile your software with countermeasures to avoid it being attacked by other programs, or wait for a chipset microcode upgrade. There are no solid Spectre fixes available yet for Intel and AMD parts.
- In terms of Intel, Googlers have found that Haswell Xeon CPUs allow user processes to access arbitrary memory; the proof-of-concept worked just within one process, though. More importantly, the Haswell Xeon also allowed a user-mode program to read kernel memory within a 4GB range on a standard Linux install.
- This is where it gets really icky. It is possible for an administrative user within a guest virtual machine on KVM to read the host server's kernel memory in certain conditions. According to Google:
When running with root privileges inside a KVM guest created using virt-manager on the Intel Haswell Xeon CPU, with a specific (now outdated) version of Debian's distro kernel running on the host, can read host kernel memory at a rate of around 1500 bytes/second, with room for optimization. Before the attack can be performed, some initialization has to be performed that takes roughly between 10 and 30 minutes for a machine with 64GiB of RAM; the needed time should scale roughly linearly with the amount of host RAM.
- AMD insists its processors are practically immune to Variant 2 Spectre attacks. As for Variant 1, you'll have to wait for microcode updates or recompile your software with forthcoming countermeasures described in the technical paper on the Spectre website.
- The researchers say AMD's Ryzen family is affected by Spectre. Googlers have confirmed AMD FX and AMD Pro cores can allow arbitrary data to be obtained by a user process; the proof-of-concept worked just within one process, though. An AMD Pro running Linux in a non-default configuration – the BPF JIT is enabled – also lets a normal user process read from 4GB of kernel virtual memory.
- For Arm, Cortex-R7, Cortex-R8, Cortex-A8, Cortex-A9, Cortex-A15, Cortex-A17, Cortex-A57, Cortex-A72, Cortex-A73, and Cortex-A75 cores are affected by Spectre.
Pelo meio têm aparecido os habituais "comentários" do Linus Torvalds

Entretanto a ARM já tem disponível uma página com a informação
https://developer.arm.com/support/security-update
EDIT: o pior para a Intel é isto vir quse 2 meses depois de ter sido descoberto um outro
Intel finds critical holes in secret Management Engine hidden in tons of desktop, server chipsets
Última edição:
A Intel já publicou quais os seus CPU afectados, pelo Meltdown
https://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00088&languageid=en-frAffected products:
For non-Intel based systems please contact your system manufacturer or microprocessor vendor (AMD, ARM, Qualcomm, etc.) for updates.
The following Intel-based platforms are impacted by this issue. Intel may modify this list at a later time. Please check with your system vendor or equipment manufacturer for more information regarding updates for your system.
Nemesis11
Power Member
supostamente com o ZEN foi introduzida uma função de "memory encription" descrita neste whitepaper.
Eu não sei encriptação de memória faria alguma coisa nestes 3 bugs. A Intel tem o SGX desde o Skylake, o Centriq da Qualcomm tem encriptação nativa nos controladores de memória e ainda não vi nada que diga que se pode mitigar esses 3 Bugs com essas opções.
Artigo sobre as duas formas da Intel e AMD: https://lwn.net/Articles/686808/
Entretanto, o Linus fez merge do Patch da AMD:
https://github.com/torvalds/linux/commit/00a5ae218d57741088068799b810416ac249a9ce
A Intel matava bem o assunto assim com uma redução apetecível nos preços e um refund a acompanhar a quem já comprou, assim uns 35% à cabeça. Pelo menos para CPU's ainda em garantia.
Alias, a redução de preço dentro dos channel/partners vai ter de acontecer, ainda mais do que já existe porque ninguém paga retail a não ser o zé povinho.
Alias, a redução de preço dentro dos channel/partners vai ter de acontecer, ainda mais do que já existe porque ninguém paga retail a não ser o zé povinho.